Container Security Market Size 2025-2029
The container security market size is forecast to increase by USD 31.24 billion at a CAGR of 49.1% between 2024 and 2029.
- The market is experiencing significant growth due to the increasing number of cyber threats targeting end-users and the widespread adoption of the Bring Your Own Device (BYOD) concept in enterprises. The integration of various security platforms, however, poses a challenge for market participants. The proliferation of cyber threats, such as container image vulnerabilities and container runtime attacks, necessitates robust container security solutions. Simultaneously, the BYOD trend, which allows employees to use their personal devices for work, increases the attack surface for organizations, necessitating effective container security measures. Furthermore, integrating multiple security platforms to ensure comprehensive container security is a complex process, requiring significant resources and expertise.
- Companies seeking to capitalize on market opportunities and navigate challenges effectively must focus on addressing these issues through innovative solutions and strategic partnerships. By prioritizing container security, organizations can protect their critical data and applications from potential threats, ensuring business continuity and maintaining customer trust.
What will be the Size of the Container Security Market during the forecast period?
- The market continues to evolve, driven by the increasing adoption of containerized applications and the complexities they introduce to security. Container security solutions encompass a range of offerings, from infrastructure security and incident response to container images, supply chain security, compliance auditing, image scanning, data encryption, and threat detection. These solutions are integrated into container orchestration platforms and security policies to safeguard cloud security and ensure adherence to compliance regulations such as PCI DSS. Security analytics, threat intelligence, and runtime security play crucial roles in identifying and mitigating risks associated with containerized environments. Container security platforms provide security dashboards for security posture management, vulnerability assessment, and security automation.
- API security, zero-trust security, and access control further bolster container security, while security awareness training and ransomware protection address human-related risks. Network security, intrusion prevention, and security testing are essential components of a comprehensive container security strategy. Red teaming and security orchestration enable organizations to simulate attacks and improve their overall security posture. Application security and security standards are also integral to maintaining the security of cloud-native applications. The dynamic nature of container security necessitates continuous monitoring, updating, and refining of security measures to address emerging threats and vulnerabilities.
How is this Container Security Industry segmented?
The container security industry research report provides comprehensive data (region-wise segment analysis), with forecasts and estimates in "USD million" for the period 2025-2029, as well as historical data from 2019-2023 for the following segments.
- Deployment
- Cloud
- On-premises
- End-user
- IT and telecom
- BFSI
- Healthcare
- Retail
- Others
- Component
- Solution
- Services
- Sector
- Large enterprises
- SMEs
- Geography
- North America
- US
- Canada
- Europe
- France
- Germany
- UK
- APAC
- Australia
- China
- India
- Japan
- South Korea
- Rest of World (ROW)
- North America
By Deployment Insights
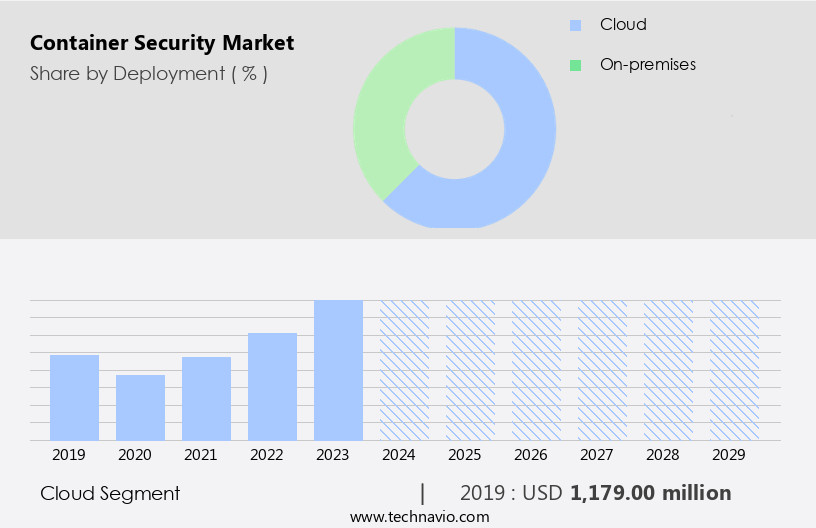
The cloud segment is estimated to witness significant growth during the forecast period.
The market is witnessing significant growth as organizations adopt containerization for cloud-native applications. Container hardening, security analytics, PCI DSS, and compliance regulations are crucial elements of container security. Container orchestration tools like Kubernetes and Docker Swarm facilitate the deployment and management of containerized applications, necessitating robust security policies and data security measures. Cloud security plays a vital role in container security as more organizations move their applications and data to cloud environments. Cloud security solutions address the protection of containerized applications and data in public, private, and hybrid clouds. These solutions encompass security analytics for threat detection, vulnerability assessment for identifying weaknesses, and runtime security for real-time threat prevention.
Security awareness training, API security, and zero-trust security are essential components of a comprehensive container security strategy. Malware detection, security monitoring, and incident response are crucial for addressing threats and maintaining a strong security posture. Risk management, intrusion prevention, and security automation are other essential aspects of container security. Container images and supply chain security are increasingly important as they can harbor vulnerabilities that could compromise the entire system. Compliance auditing, image scanning, data encryption, and threat detection are vital practices for maintaining container security. Network security, red teaming, security orchestration, application security, and access control are additional areas of focus for container security platforms.
Infrastructure security and incident response are essential for addressing security incidents and maintaining business continuity.
The Cloud segment was valued at USD 1.18 billion in 2019 and showed a gradual increase during the forecast period.
Regional Analysis
APAC is estimated to contribute 39% to the growth of the global market during the forecast period.Technavio's analysts have elaborately explained the regional trends and drivers that shape the market during the forecast period.
The market in North America is experiencing steady growth, with a significant focus in the US. Factors driving this expansion include the increasing adoption of container security by industries, the transition of traditional IT services to cloud-based systems, the growth of end-user sectors, and government initiatives promoting container security implementation. Despite economic saturation in the US, the market is anticipated to continue its growth trajectory due to regulatory pressures and the increasing number of IT companies and start-ups. Container hardening, security analytics, and PCI DSS compliance are essential aspects of container security. Container orchestration and security policies ensure the secure deployment and management of cloud-native applications.
Data security, cloud security, and compliance regulations are critical concerns for organizations utilizing container technology. Threat intelligence and container security solutions provide vital protection against malware and intrusions. Penetration testing, security posture management, and security dashboards help organizations assess vulnerabilities and monitor their security posture. Vulnerability assessment and runtime security offer real-time protection against threats. Zero-trust security, risk management, and intrusion prevention are essential for securing container environments. Security automation and ransomware protection are crucial for maintaining business continuity. Network security, red teaming, security orchestration, application security, security standards, access control, container security platforms, infrastructure security, and incident response are all integral components of a robust container security strategy.
Container images and supply chain security are essential for maintaining the integrity of the container ecosystem. Compliance auditing, image scanning, data encryption, and threat detection are essential practices for ensuring regulatory compliance and securing sensitive data.
Market Dynamics
Our researchers analyzed the data with 2024 as the base year, along with the key drivers, trends, and challenges. A holistic analysis of drivers will help companies refine their marketing strategies to gain a competitive advantage.
What are the key market drivers leading to the rise in the adoption of Container Security Industry?
- The escalating prevalence of cyber threats among end-users serves as the primary catalyst for market growth.
- Container security is a critical issue in today's digital landscape, with cyber threats continually evolving and increasing in frequency and sophistication. According to recent research, there was a significant surge in data breaches in 2024, with approximately 422.61 million data records leaked in various incidents, impacting millions of individuals worldwide. These breaches involved various organizations, from healthcare providers like Medusind Inc., which experienced a cyberattack resulting in the exposure of personal, health, and billing information for 360,000 individuals, to telecommunications giants such as AT&T, where cybercriminals stole phone numbers and call records of nearly all its customers, affecting around 110 million people.
- To mitigate these risks, organizations must prioritize security posture management and adopt a proactive approach to container security. This includes implementing security dashboards for real-time visibility into container environments, conducting regular vulnerability assessments, and deploying runtime security solutions. Additionally, security awareness training for employees is essential to prevent human error and insider threats. Cloud-native applications and APIs are increasingly being targeted by cybercriminals, making security a top priority for organizations adopting these technologies. Malware detection and security monitoring are crucial components of container security, along with implementing zero-trust security models to ensure that only authorized users and applications have access to sensitive data.
- Furthermore, integrating security into the CI/CD pipeline is essential to ensure that security checks are performed at every stage of the development process.
What are the market trends shaping the Container Security Industry?
- The BYOD (Bring Your Own Device) trend is gaining significant traction in enterprises, serving as a notable market development. This increasing adoption of personal devices for professional use is a key trend in the business world.
- Container security has emerged as a critical concern for businesses as they adopt cloud-native technologies and DevOps practices. With the increasing use of containers in deploying applications, the risk of intrusions and data breaches has grown. According to recent research, the market is expected to grow significantly due to the need for advanced risk management solutions. Security automation is a key trend in container security, enabling continuous security testing and vulnerability scanning. Ransomware protection is another priority area, as containers are vulnerable to malware attacks. Network security and access control are essential components of container security, ensuring that only authorized users and applications can access the containers.
- Red teaming and security orchestration are becoming increasingly popular as organizations seek to simulate real-world attacks and improve their incident response capabilities. Application security is also a critical concern, as containers can be used to deploy vulnerable applications that can put the entire infrastructure at risk. Security standards such as ISO 27001 and NIST are driving the adoption of container security solutions. Intrusion prevention and security testing are essential to maintaining compliance with these standards and protecting against emerging threats. In conclusion, the market is expected to grow significantly due to the increasing adoption of containerized applications and the need for advanced security solutions.
- Organizations must prioritize risk management, intrusion prevention, security automation, ransomware protection, security testing, network security, access control, and application security to ensure the security of their containerized environments.
What challenges does the Container Security Industry face during its growth?
- The integration complexities in security platforms represent a significant challenge that can hinder industry growth. It is essential for organizations to address these issues effectively to ensure seamless system compatibility and maintain optimal security measures.
- Container security is a critical concern for organizations as they adopt containerized infrastructure. The integration of container security platforms with existing infrastructure can pose challenges due to compatibility issues between hardware and software. Many security solutions available in the market are stand-alone, making it difficult to integrate them with other security solutions. Moreover, customized solutions are not cost-effective and may not meet the end-users' limited requirements. These factors discourage organizations from implementing container security solutions, impacting the revenue growth in the market. Container security platforms play a crucial role in securing infrastructure against threats. Incident response, container image scanning, supply chain security, compliance auditing, data encryption, and threat detection are essential features of these platforms.
- However, the integration of these solutions with existing infrastructure can be complex due to compatibility issues. Organizations are increasingly focusing on container security to protect their infrastructure against cyber threats. Container images, which form the foundation of containerized applications, are susceptible to vulnerabilities. Supply chain security is another critical aspect of container security, as attacks can occur at any stage of the container development and deployment process. Compliance auditing and image scanning are essential to ensure the security of container images and maintain regulatory compliance. Data encryption and threat detection are crucial features that help protect data and prevent unauthorized access to containers.
- Despite the benefits of container security platforms, organizations face challenges in implementing them due to integration issues. Standard products with compatibility criteria for hardware and software can help address these challenges and encourage wider adoption of container security solutions.
Exclusive Customer Landscape
The container security market forecasting report includes the adoption lifecycle of the market, covering from the innovator's stage to the laggard's stage. It focuses on adoption rates in different regions based on penetration. Furthermore, the container security market report also includes key purchase criteria and drivers of price sensitivity to help companies evaluate and develop their market growth analysis strategies.
Customer Landscape
Key Companies & Market Insights
Companies are implementing various strategies, such as strategic alliances, container security market forecast, partnerships, mergers and acquisitions, geographical expansion, and product/service launches, to enhance their presence in the industry.
Anchore Inc. - The company specializes in container security solutions, providing advanced technologies such as Aqua DTA, Aqua Risk Explorer, and Aqua vShield. These offerings scan container images utilizing a continuous feed of vulnerability data from diverse sources. By leveraging this comprehensive data stream, the company ensures container security remains robust and up-to-date. This proactive approach minimizes potential risks, safeguarding applications and infrastructure from evolving threats.
The industry research and growth report includes detailed analyses of the competitive landscape of the market and information about key companies, including:
- Anchore Inc.
- Aqua Security Software Ltd.
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems Inc.
- CrowdStrike Inc.
- Docker Inc.
- Fortra LLC
- International Business Machines Corp.
- Lacework
- Microsoft Corp.
- Musarubra US LLC
- Palo Alto Networks Inc.
- Qualys Inc.
- Rapid7 Inc.
- Sonatype Inc.
- Sophos Ltd.
- Sysdig Inc.
- Trend Micro Inc.
- XenonStack
Qualitative and quantitative analysis of companies has been conducted to help clients understand the wider business environment as well as the strengths and weaknesses of key industry players. Data is qualitatively analyzed to categorize companies as pure play, category-focused, industry-focused, and diversified; it is quantitatively analyzed to categorize companies as dominant, leading, strong, tentative, and weak.
Recent Development and News in Container Security Market
- In February 2024, Palo Alto Networks, a leading cybersecurity company, announced the launch of its new container security solution, Prisma for Containers, which uses machine learning and behavioral analysis to secure containerized applications (Palo Alto Networks Press Release, 2024). This development signified a significant advancement in container security, as the solution aimed to address the increasing threat of container attacks.
- In June 2025, IBM and Red Hat, two major technology companies, announced a strategic partnership to integrate IBM's security solutions with Red Hat's OpenShift container platform. This collaboration was expected to enhance container security by providing advanced threat protection and compliance capabilities (IBM Press Release, 2025). The partnership was a notable development, as it combined the strengths of both companies to address the growing demand for secure containerization in enterprise environments.
- In October 2024, Aqua Security, a container security company, secured a USD100 million Series D funding round, led by Insight Partners. This investment was a significant milestone for Aqua Security, as it brought the company's total funding to USD230 million and positioned it as a major player in the market (Aqua Security Press Release, 2024). The funding would be used to expand the company's global presence, accelerate product development, and enhance its sales and marketing efforts.
- In December 2025, the European Union Agency for Cybersecurity (ENISA) published a report on container security, emphasizing the importance of securing containerized applications in the European Union. The report recommended the adoption of security best practices, such as implementing container runtime security and network segmentation, to mitigate the risks associated with containerization (ENISA Report, 2025). This regulatory initiative was a significant development, as it highlighted the growing concern over container security in Europe and the need for organizations to prioritize this area.
Research Analyst Overview
Container security continues to be a top priority for businesses adopting containerized applications. With the increasing use of containerization, the number of reported security incidents, such as container security breaches, has risen. To mitigate these risks, organizations turn to container security solutions, including container isolation and security orchestration platforms. Security testing methodologies, threat analysis, and open source security play crucial roles in identifying and addressing vulnerabilities. Container security certifications, data loss prevention, and container security frameworks are essential components of a robust container security roadmap. Container security challenges extend beyond container security tools and include security configuration, container registry security, and security event management.
Host security, security automation tools, and security intelligence are also integral to a comprehensive container security strategy. Container security companies offer various solutions to help businesses navigate the complex container security landscape. Container lifecycle management is a critical aspect of container security, ensuring secure deployment, configuration, and maintenance of containers throughout their lifecycle.
Dive into Technavio's robust research methodology, blending expert interviews, extensive data synthesis, and validated models for unparalleled Container Security Market insights. See full methodology.
|
Market Scope |
|
|
Report Coverage |
Details |
|
Page number |
237 |
|
Base year |
2024 |
|
Historic period |
2019-2023 |
|
Forecast period |
2025-2029 |
|
Growth momentum & CAGR |
Accelerate at a CAGR of 49.1% |
|
Market growth 2025-2029 |
USD 31240.3 million |
|
Market structure |
Fragmented |
|
YoY growth 2024-2025(%) |
38.1 |
|
Key countries |
US, Canada, UK, China, Germany, Japan, India, France, South Korea, and Australia |
|
Competitive landscape |
Leading Companies, Market Positioning of Companies, Competitive Strategies, and Industry Risks |
What are the Key Data Covered in this Container Security Market Research and Growth Report?
- CAGR of the Container Security industry during the forecast period
- Detailed information on factors that will drive the growth and forecasting between 2025 and 2029
- Precise estimation of the size of the market and its contribution of the industry in focus to the parent market
- Accurate predictions about upcoming growth and trends and changes in consumer behaviour
- Growth of the market across North America, APAC, Europe, Middle East and Africa, and South America
- Thorough analysis of the market's competitive landscape and detailed information about companies
- Comprehensive analysis of factors that will challenge the container security market growth of industry companies
We can help! Our analysts can customize this container security market research report to meet your requirements.